GSM SIM Card is Finally Hacked, Puts 750 Million Users at Risk

The SIM was one of the few common things in tech which were considered impossible to hack. Until now. Karsten Nohl of Security Research Labs (based out of Germany) has finally got a way past the 56-digit unique code and found a simple process which leaves an estimated 750 million SIM cards at risk.
The research was done on a 1000 SIM cards and only the ones which were using the old DES (Data Encryption Standard) standard were found vulnerable. Cracking them is super-easy and takes just 2 minutes. A message is sent to the target SIM card while disguised as the carrier. In response, a message is received containing information needed to find a way past the 56-digit code or the digital key which can allow the hacker to take control of the target SIM.
After getting this information and taking control, the intruder can easily listen to your calls, send text messages and in short, have control over every form of data on your SIM card.
Mr. Nohl said:
“We can spy on you. We know your encryption keys for calls. We can read your S.M.S.’s. More than just spying, we can steal data from the SIM card, your mobile identity, and charge to your account.”
In all, about 25% of the SIM cards which were tested were found susceptible to such penetration. Newer technologies like NFC might be at risk too.
D.E.S. encryption, which is vulnerable to such hacks – is used on about half of the about six billion cellphones. Over the past decade, most operators have adopted a stronger encryption method, called Triple D.E.S., but many SIM cards still run the old standard.
The GSM Association hasn’t confirmed this just yet though as it will investigate the case first but if this, in any way is true, it will pose some serious threats to people using SIM card for much more complex purposes than calling and texting. Mobile payments that is.
4 Ways to Crack a Facebook Password and How to Protect Yourself from Them
espite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over one billion monthly active users as of October 2012—and around 600 million active daily users.
We share our lives on Facebook. We share our birthdays and our anniversaries. We share our vacation plans and locations. We share the births of our sons and the deaths of our fathers. We share our most cherished moments and our most painful thoughts. We divulge every aspect of our lives.
But we sometimes forget who's watching.
We use Facebook as a tool to connect, but there are those people who use that connectivity for malicious purposes. We reveal what others can use against us. They know when we're not home and for how long we're gone. They know the answers to our security questions. People can practically steal our identities—and that's just with the visible information we purposely(?) give away through our public Facebook profile.
The scariest part is that as we get more comfortable with advances in technology, we actually become more susceptible to hacking. As if we haven't already done enough to aid hackers in their quest for our data by sharing publicly, those in the know can get into our emails and Facebook accounts to steal every other part of our lives that we intended to keep away from prying eyes.
In fact, you don't even have to be a professional hacker to get into someone's Facebook account.
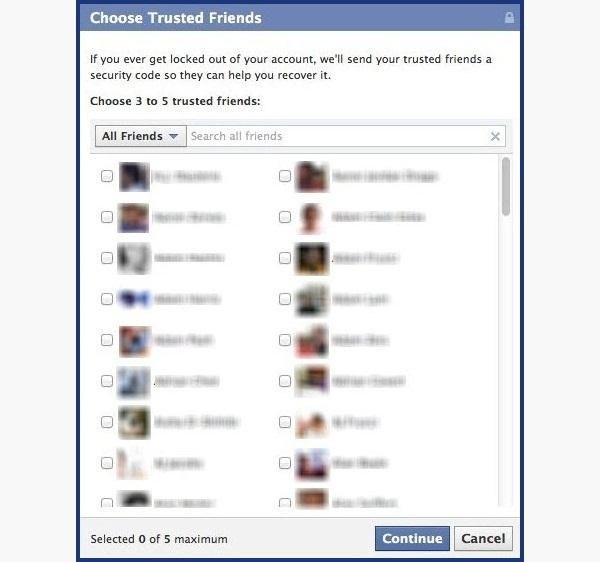
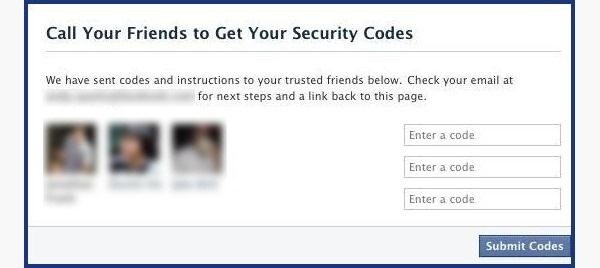
It can be as easy as running Firesheep on your computer for a few minutes. In fact, Facebook actually allows people to get into someone else's Facebook account without knowing their password. All you have to do is choose three friends to send a code to. You type in the three codes, and voilà—you're into the account. It's as easy as that.
In this article I'll show you these, and a couple other ways that hackers (and even regular folks) can hack into someone's Facebook account. But don't worry, I'll also show you how to prevent it from happening to you.
Method 1: Reset the Password
The easiest way to "hack" into someone's Facebook is through resetting the password. This could be easier done by people who are friends with the person they're trying to hack.
- The first step would be to get your friend's Facebook email login. If you don't already know it, try looking on their Facebook page in the Contact Info section.
- Next, click on Forgotten your password? and type in the victim's email. Their account should come up. Click This is my account.
- It will ask if you would like to reset the password via the victim's emails. This doesn't help, so press No longer have access to these?
- It will now ask How can we reach you? Type in an email that you have that also isn't linked to any other Facebook account.
- It will now ask you a question. If you're close friends with the victim, that's great. If you don't know too much about them, make an educated guess. If you figure it out, you can change the password. Now you have to wait 24 hours to login to their account.
- If you don't figure out the question, you can click on Recover your account with help from friends. This allows you to choose between three and five friends.
- It will send them passwords, which you may ask them for, and then type into the next page. You can either create three to five fake Facebook accounts and add your friend (especially if they just add anyone), or you can choose three to five close friends of yours that would be willing to give you the password.
How to Protect Yourself
- Use an email address specifically for your Facebook and don't put that email address on your profile.
- When choosing a security question and answer, make it difficult. Make it so that no one can figure it out by simply going through your Facebook. No pet names, no anniversaries—not even third grade teacher's names. It's as easy as looking through a yearbook.
- Learn about recovering your account from friends. You can select the three friends you want the password sent to. That way you can protect yourself from a friend and other mutual friends ganging up on you to get into your account.
Method 2: Use a Keylogger
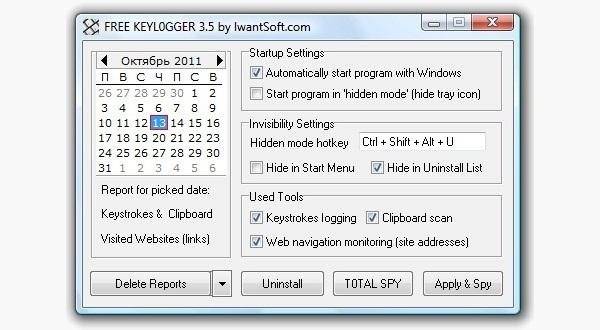
Software Keylogger
A software keylogger is a program that can record each stroke on the keyboard that the user makes, most often without their knowledge. The software has to be downloaded manually on the victim's computer. It will automatically start capturing keystrokes as soon as the computer is turned on and remain undetected in the background. The software can be programmed to send you a summary of all the keystrokes via email.
CNET has Free Keylogger, which as the title suggests, is free. If this isn't what you're looking for, you can search for other free keyloggers or pay for one.
Hardware Keylogger
These work the same way as the software keylogger, except that a USB drive with the software needs to be connected to the victim's computer. The USB drive will save a summary of the keystrokes, so it's as simple as plugging it to your own computer and extracting the data. You can look through Keelog for prices, but it's bit higher than buying the software since you have the buy the USB drive with the program already on it.
How to Protect Yourself
- Use a firewall. Keyloggers usually send information through the internet, so a firewall will monitor your computer's online activity and sniff out anything suspicious.
- Install a password manager. Keyloggers can't steal what you don't type. Password mangers automatically fill out important forms without you having to type anything in.
- Update your software. Once a company knows of any exploits in their software, they work on an update. Stay behind and you could be susceptible.
- Change passwords. If you still don't feel protected, you can change your password bi-weekly. It may seem drastic, but it renders any information a hacker stole useless.
Method 3: Phishing
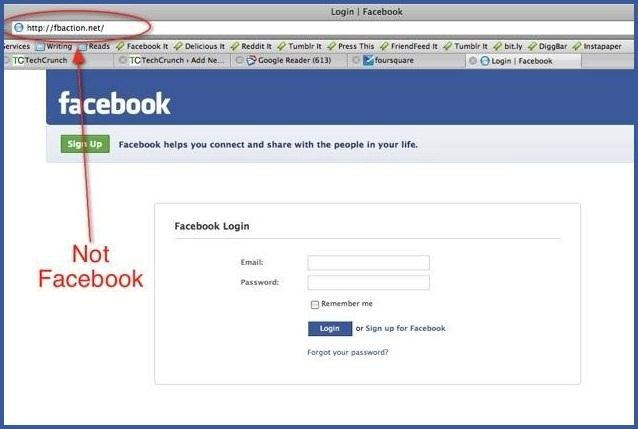
This option is much more difficult than the rest, but it is also the most common method to hack someone's account. The most popular type ofphishing involves creating a fake login page. The page can be sent via email to your victim and will look exactly like the Facebook login page. If the victim logs in, the information will be sent to you instead of to Facebook. This process is difficult because you will need to create a web hosting account and a fake login page.
If you want to know how to do this, follow the detailed instructions onHacker9's website. Users are very careful now with logging into Facebook through other links, though, so that only adds to this already difficult process.
How to Protect Yourself
- Don't click on links through email. If an email tells you to login to Facebook through a link, be wary. Check the URL. If you're still doubtful, go directly to the main website and login the way you always do.
- Phishing isn't only done through email. It can be any link on any website. Even ads that pop up can be malicious. Don't click on any sketchy looking links that ask for your information.
- Use an anti-virus like Norton or McAfee.
Method 4: Stealing Cookies
Cookies allow a website to store information on a user's hard drive and later retrieve it. These cookies contain important information that a hacker can sniff out and steal if they are on the same Wi-Fi network as the victim. They don't actually get the login passwords, but they can still access the victim's account.
Firesheep is a Firefox add-on that sniffs web traffic on an open Wi-Fi connection. It collects the cookies and stores them in a tab on the side of the browser.
From there, the hacker can click on the saved cookies and access the victim's account, as long as the victim is still logged in. Once the victim logs out, it is impossible for the hacker to access the account.
How to Protect Yourself
- On Facebook, go to your Account Settings and check under Security. Make sure Secure Browsing is enabled. Firesheep can't sniff out cookies on HTTPS, so try to steer away from HTTP.
- Full time SSL. Use Firefox add-ons such as HTTPS-Everywhere or Force-TLS.
- Log off a website when you're done. Firesheep can't stay logged in to your account if you log off.
- Use only trustworthy Wi-Fi networks. A hacker can be sitting across from you at Starbucks and looking through your email without you knowing it.
- Use a VPN. These protect against any sidejacking no matter what website you're on.
Protecting Yourself: Less Is More
Social networking websites are great ways to stay connected with old friends and meet new people. Creating an event, sending a birthday greeting and telling your parents you love them are all a couple of clicks away.
Facebook isn't something you should steer away from, but you do need to be aware of your surroundings and make smart decisions about what you put up on your profile. The less information you give out on Facebook for everyone to see, the more difficult you make it for hackers.
Password Protect Any Folder Without Any Software

In my previous post i have teach you to hide files behind images. In this tutorial i will show you interesting and useful trick to password protect folder without using any software using batch file programming. This trick will work on all windows platform (Win XP, Win 7). Follow below tutorial to learn this trick.
How To Lock Folder ?
1. Open Notepad and Copy code given below into it.
cls
@ECHO OFF
title coolhacking-tricks.blogspot.com
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST MyFolder goto MDMyFolder
:CONFIRM
echo Are you sure to lock this folder? (Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren MyFolder "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock Your Secure Folder
set/p "pass=>"
if NOT %pass%== zeehack goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" MyFolder
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDMyFolder
md MyFolder
echo MyFolder created successfully
goto End
:End
3. Now double click on lock.bat and a new folder will be created with name MyFolder
4. Copy all your data you want to protect in that New folder
5. Now double click on lock.bat and when command promp appears Type Y and press enter.
6. Now MyFolder will be hidden from you view, to access that folde double click on lock.bat
7. It will ask for password enter your password and done. (Default password is zeehack)
To change the password replace zeehack with new password in the above code
How To Further Secure ?
You might be thinking that anyone can access the password by opening that lock.bat file in Notepad or any other text editor. To make it more secure hide lock.bat in some secure location after following the above tutorial To access the secured file double click on lock.bat. I would suggest copying lock.bat file into Pen drive and copying it into your computer whenever you required to access to your protected files.
Warid Brings International Prepaid Data Roaming Service
If you are planning to travel abroad with your Warid SIM where you could surf online, download apps or browse on Facebook while using Warid’s speedy data service. For the first time in Pakistan, Warid has brought a facility for prepaid subscribers roaming abroad.
| PREPAID GPRS ROAMING – WARID | |||||||
| Country | Operator | Network Code | Uplink charges | Downlink charges | MMS | Charging interval | Helpline |
| Saudi Arabia | Etihad Etisalat | 420-03 | $0.002 | $0.002 | $0.57 | 10 KB | +96265828100 |
| Saudi Arabia | Al Jawal | 420-01 | $0.023 | $0.023 | $6.96 | 10 KB | +96614555555 |
| Saudi Arabia | Zain | 420-04 | $0.023 | $0.023 | $6.96 | 10 KB | Not available |
| UAE | Du | 424-03 | $0.001 | $0.001 | $0.21 | 1KB | +971555555177 |
| UAE | Etisalat | 424-02 | $0.022 | $0.022 | $6.54 | 30 KB | +9714004101 |
Please note that in order to avoid over billing issues, smart phone users can anytime disconnect Data Connection/Cellular Data option to prevent auto sync.
Terms and Conditions:
- To get Prepaid International Roaming activated, please call 321.
- No security deposit required.
- Operator specific GPRS usage rates shall apply.
- All applicable taxes would be included in addition to the above rates.
- The tariffs are charged in Pak Rupees when billed. The US$ – Pak Rupee exchange rate applied for each calendar month shall be the open market exchange rate on 23rd day of the preceding month.
- GPRS charges have been calculated using prevailing exchange rates and are subject to change without prior notice.
- Above GPRS charges are shown in 1KB increments. For operator specific charging interval, please refer to the Charging Interval column above.
- For detailed tariffs/peak hour timings of a specific network, contact the Customer Service personnel and the helpline number of the respective operator.
- MMS charges are event based.
- For more information, please call 321.
Online Sim Information System

Pakistan Telecommunication Authority (PTA) has developed a SIM (Subscriber Identity Module) information system to address associated risks on security and to ensure subscription regulations in cellular sector.
+copy.jpg)